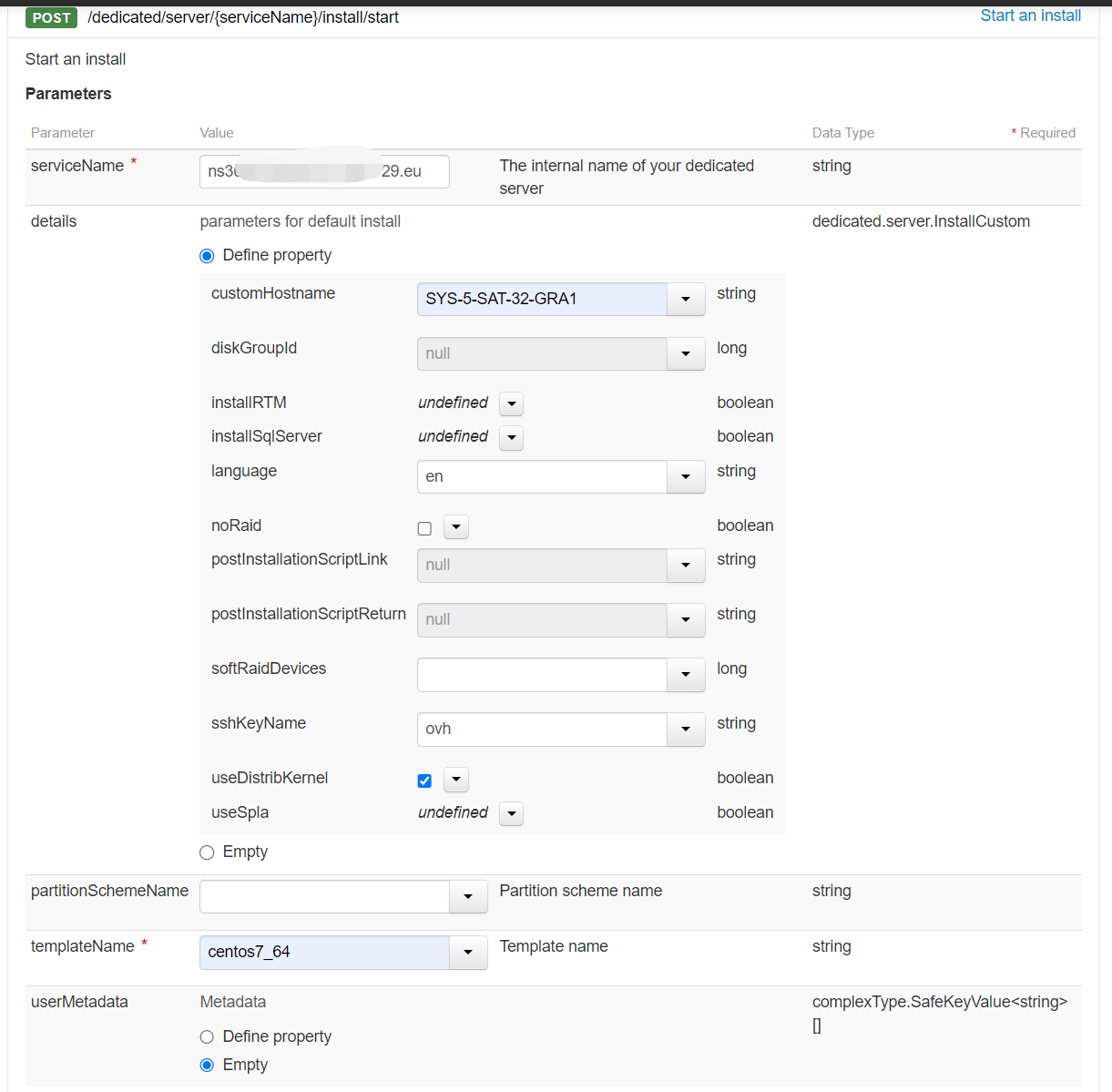
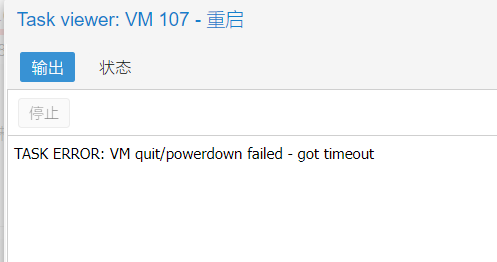
OVH的新面板提供的系统模板比较少,想装CENTOS 8 STREAM都没有,拿到的这台机器IPMI一挂载ISO就崩溃闪...
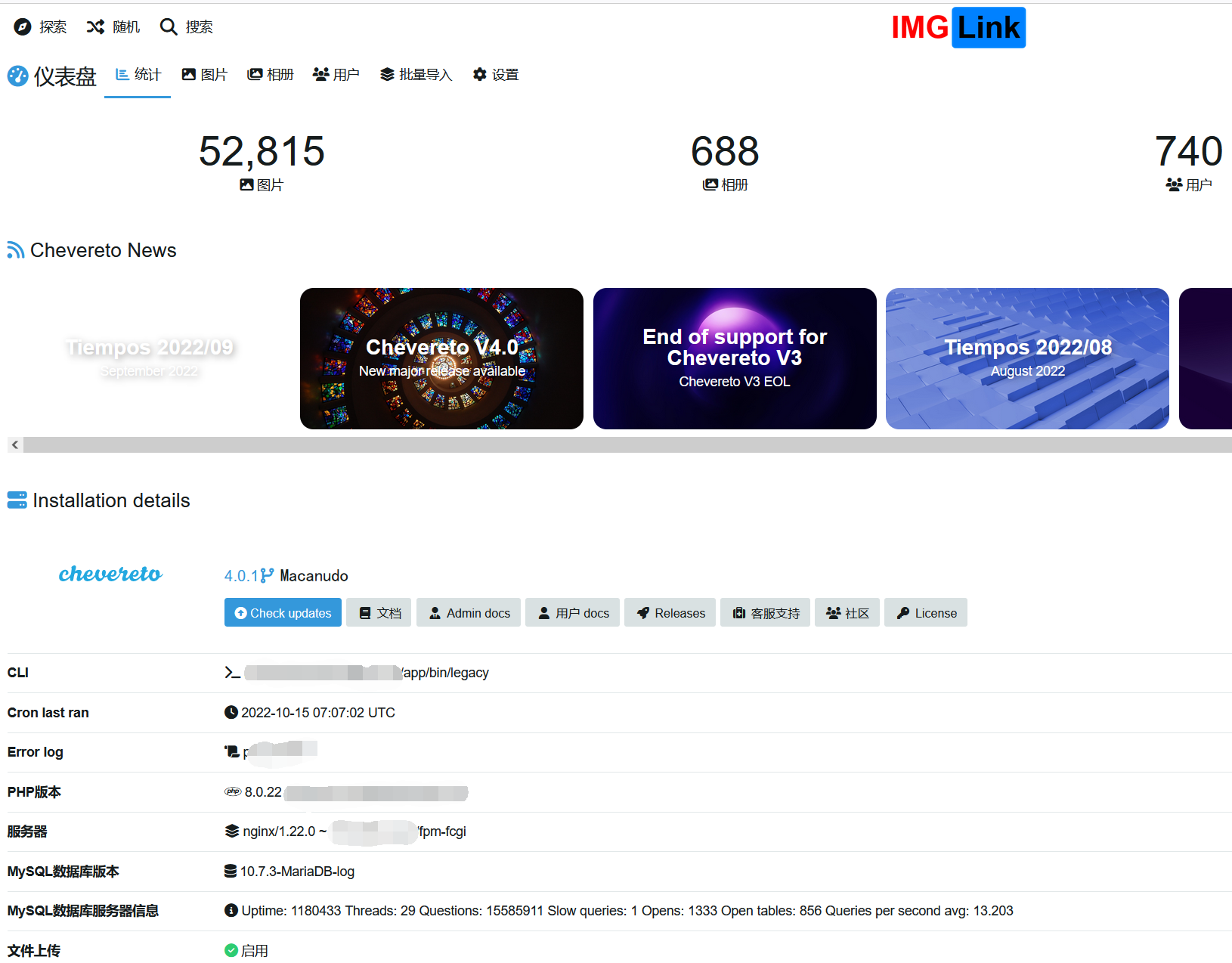
Chevereto将在11月终止维护V3版本,于是考虑升级为V4,之前有尝试新装V4进行测试,使用DOCKER没有问题,...
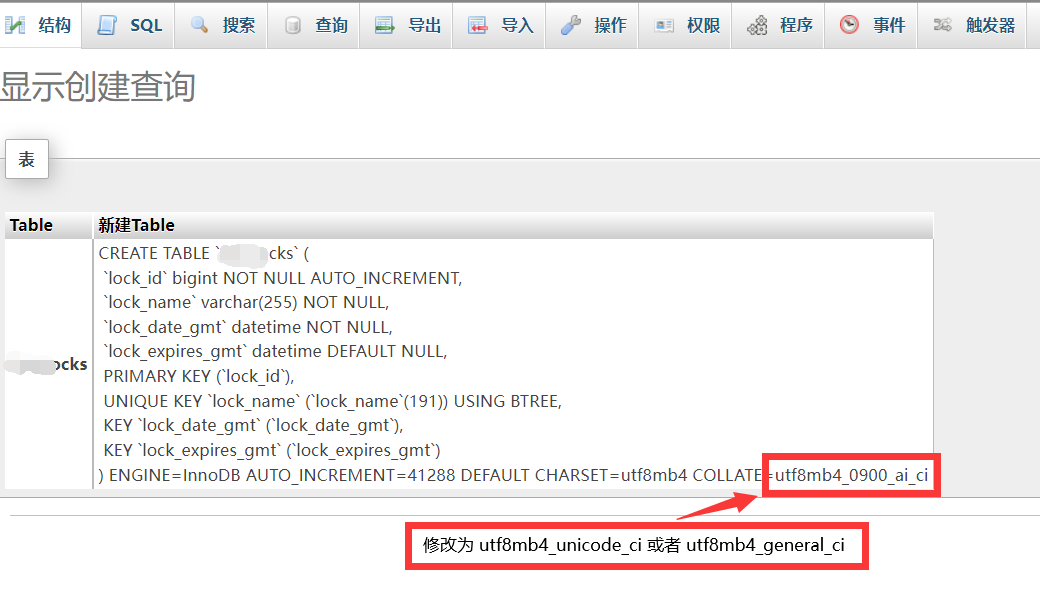
Chevereto的数据库从MySQL 8迁移至MariaDB 10可能会导致表缺失。昨晚将图床服务器从美西迁移到OVH...
最近黑五OVH特价更新了KS产品线,其中最具性价比的新一代神机KS-LE一下就被抢购一空,不少人开到了中奖机上下G口,我...